Smart switches and plugs contribute significantly to home security, extending far beyond simple convenience features. When strategically implemented, these devices create a comprehensive security ecosystem that deters intruders, provides peace of mind, and protects your property whether you’re home or away. This exploration of security-focused applications demonstrates how these affordable, accessible devices can form the foundation of an effective home protection strategy.

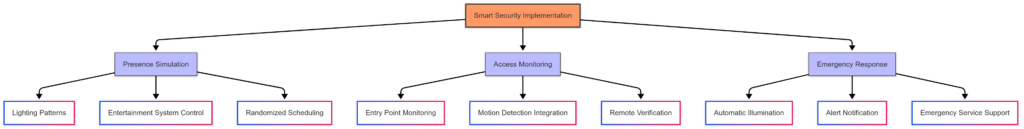
Presence Simulation Fundamentals
Creating the impression of occupancy is a powerful deterrent to potential intruders.
Smart Device Security Considerations
Lighting-Based Simulation
Mimic natural human presence through strategic lighting control:
Natural Pattern Replication:
- Vary activation times slightly each day
- Create room-to-room movement sequences
- Implement gradual brightness changes
- Avoid perfectly consistent timing that appears automated
Lifestyle-Based Programming:
- Morning routine lighting sequences
- Evening arrival illumination patterns
- Weekend vs. weekday variations
- Seasonal adjustments for changing daylight hours
Strategic Fixture Selection:
- Prioritize visible-from-street lighting
- Include both interior and exterior fixtures
- Incorporate multiple rooms for realistic effect
- Consider window treatments in coordination with lighting
Beyond Basic Lighting
Expand presence simulation to multiple device types:
Entertainment System Activation:
- TV power cycling during typical viewing hours
- Audio system operation at appropriate times
- Screen glow effects visible from windows
- Volume settings that suggest occupancy without disturbing neighbors
Daily Activity Simulation:
- Kitchen appliance operation during meal times
- Bathroom fan activation following typical schedules
- Home office equipment during working hours
- Laundry room activity on usual laundry days
Environmental Control Patterns:
- HVAC system adjustments mimicking occupancy
- Ceiling fan operation in visible rooms
- Window treatment automation (if integrated)
- Exterior feature activation (fountains, landscape lighting)
Advanced Security Integration
Smart switches and plugs enhance traditional security systems.
Security System Coordination
Create complementary protection layers:
Alarm Event Responses:
- Full property illumination when alarms trigger
- Specific pathway lighting for emergency exit
- Attention-drawing exterior light patterns
- Power activation for emergency communication devices
Monitoring Enhancement:
- Improved visibility for security cameras
- Strategic lighting to eliminate shadowed areas
- Power management for continuous camera operation
- Automated recording device activation
Deterrent Escalation:
- Progressive lighting activation when motion is detected
- Coordinated audio system alerts or warnings
- Simulated conversation or activity sounds
- Sequential exterior-to-interior lighting suggesting awareness
Sensor-Triggered Automation
Leverage various sensors for comprehensive awareness:

We offer a wide range of smart sensors to meet your needs.
Motion Detection Integration:
- Immediate lighting response to unexpected movement
- Differentiated reactions based on location and time
- Sequential activation following movement patterns
- Alert notification through connected devices
Door and Window Sensors:

We offer Zigbee Wireless door/window sensors
- Immediate illumination when entry points activate
- Distinctive patterns for different access points
- Escalating response for repeated or multiple activations
- Time-appropriate reactions (subtle at night, full during day)
Environmental Trigger Responses:
- Smoke/CO detector coordinated lighting for evacuation
- Water leak detector pump or valve activation
- Temperature anomaly responses
- Weather event preparation sequences
Remote Monitoring and Control
Maintain awareness and control from anywhere:
Real-Time Observation:
- Live status monitoring of all connected devices
- Activity logs with timestamp documentation
- Power consumption patterns indicating usage
- Anomaly alerts for unexpected activity
On-Demand Control:
- Immediate full property illumination capability
- Room-by-room remote activation
- Scenario-based emergency configurations
- Verification capabilities after alert notifications
Automated Documentation:
- Event recording with detailed timestamps
- Power state change history
- Activation pattern logging
- Integration with security system event records
Implementation Strategies
Effective security applications require thoughtful planning and execution.
Vulnerability Assessment
Identify and address security weaknesses:
Property Evaluation:
- Identify poorly illuminated exterior areas
- Note secluded entry points requiring attention
- Assess interior visibility from outside
- Evaluate existing security measure effectiveness
Routine Analysis:
- Document typical household schedules and patterns
- Identify predictable absences requiring coverage
- Note seasonal vulnerability changes
- Consider special circumstances (vacations, business travel)
Neighborhood Context:
- Understand area-specific security concerns
- Note nearby properties with existing security measures
- Identify neighborhood-specific vulnerability patterns
- Consider community security resources and limitations
Strategic Device Placement
Position devices for maximum security impact:
Exterior Priorities:
- Entry point coverage (doors, accessible windows)
- Driveway and walkway illumination
- Property boundary definition
- Elimination of concealment areas
Interior Considerations:
- Window-visible fixtures for presence simulation
- Sequential path coverage for realistic movement
- Critical area monitoring (home office, valuables)
- Emergency exit path illumination
Layered Coverage Design:
- Overlapping zones of protection
- Redundancy for critical areas
- Varied device types for comprehensive coverage
- Backup power for essential security elements
Automation Rule Development
Create effective security-focused automations:
Trigger Diversity:
- Time-based activations for predictable patterns
- Sensor-initiated responses for unexpected events
- Location-based triggers (geofencing)
- System state changes (alarm activation, mode changes)
Response Appropriateness:
- Subtle nighttime reactions to avoid sleep disruption
- Attention-grabbing responses to potential threats
- Contextual awareness of normal vs. abnormal events
- Escalation paths for repeated or serious triggers
Scenario-Based Planning:
- Vacation mode comprehensive coverage
- Nighttime security enhancement
- Working hours protection
- Unexpected return preparation
Specialized Security Applications
Certain situations benefit from tailored approaches.
Vacation and Extended Absence Protection
Comprehensive coverage during longer periods away:
Progressive Pattern Evolution:
- Gradually changing routines throughout absence
- Varied timing to avoid predictable patterns
- Multiple room involvement for realistic effect
- Seasonal appropriateness throughout duration
Supplemental Monitoring Integration:
- Coordination with professional monitoring services
- Neighbor or property manager notification capabilities
- Remote verification options
- Backup system engagement during power or network issues
Return Preparation Sequences:
- Pre-arrival environment preparation
- Safety verification procedures
- Gradual return to normal operation patterns
- Post-absence security status reporting
Family Safety Enhancement
Protection for household members beyond intrusion prevention:
Child Safety Applications:
- After-school arrival verification
- Restricted device access scheduling
- Safe path illumination for nighttime navigation
- Emergency help request capability
Elder Care Support:
- Routine verification through device usage patterns
- Simplified emergency lighting activation
- Fall risk reduction through pathway illumination
- Caregiver notification based on activity patterns
Health Emergency Assistance:
- Emergency services guidance lighting
- Medical device power backup
- Critical notification system support
- Access facilitation for emergency responders
Severe Weather and Disaster Preparation
Security during environmental emergencies:
Power Outage Management:
- Essential device backup power prioritization
- Automatic power restoration procedures
- Low-power emergency mode activation
- Critical system maintenance during extended outages
Evacuation Support:
- Clear path illumination to exits
- Guided routing through sequential activation
- Emergency supply area highlighting
- Exterior gathering point illumination
Return and Recovery Assistance:
- Safe re-entry pathway identification
- Damage assessment illumination
- Recovery equipment power management
- Temporary security measure implementation
Privacy and Ethical Considerations
Responsible security implementation requires careful attention to privacy.
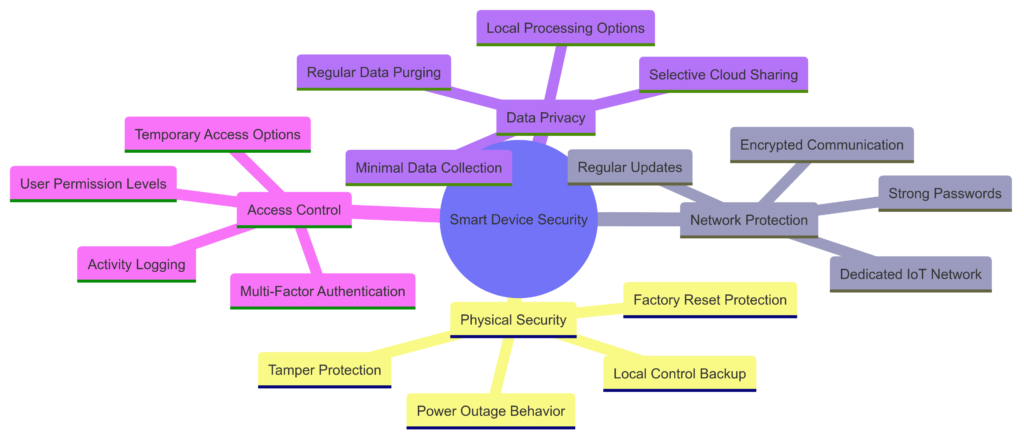
Data Security Best Practices
Protect the systems that protect you:
Network Security Fundamentals:
- Dedicated IoT network separation
- Strong, unique passwords for all devices
- Regular firmware and software updates
- Two-factor authentication when available
Information Protection:
- Minimal data collection configuration
- Local processing preference over cloud when available
- Regular deletion of unnecessary historical data
- Encrypted storage and transmission
Access Control Management:
- Strict permission limitations for shared access
- Regular review of authorized users
- Immediate removal of temporary access
- Detailed audit logging of system changes
Neighbor and Community Considerations
Implement security without creating nuisance:
Light Pollution Minimization:
- Directional lighting to avoid spillover
- Brightness limitations during overnight hours
- Motion activation rather than constant illumination
- Thoughtful color temperature selection
Notification Discretion:
- Appropriate alert sound levels
- Careful placement of audible notifications
- Time-appropriate alert methods
- Graduated response severity
Shared Resource Respect:
- Bandwidth consideration for network-intensive features
- Power consumption awareness during grid stress
- Coordination with community security initiatives
- Information sharing with appropriate privacy boundaries
Avoiding False Security
Recognize and address system limitations:
Supplemental Measure Awareness:
- Understanding smart devices as one security layer
- Appropriate integration with traditional security measures
- Recognition of connectivity vulnerabilities
- Backup procedures for system failures
Testing and Verification:
- Regular security scenario testing
- Periodic effectiveness evaluation
- Unexpected pattern auditing
- Vulnerability assessment updates
Continuous Improvement Process:
- Security measure evolution as technology changes
- Threat landscape awareness and adaptation
- Regular review of new capabilities and features
- Community and professional resource consultation
Future Security Enhancements
Emerging technologies will expand smart device security capabilities.
AI and Machine Learning Integration
Intelligent systems will provide more sophisticated protection:
Behavioral Pattern Recognition:
- Normal household routine learning
- Anomaly detection without explicit programming
- Continuous adaptation to changing patterns
- Reduced false alarms through contextual understanding
Predictive Security Measures:
- Anticipatory responses to developing situations
- Risk factor analysis and proactive adjustment
- Seasonal and environmental adaptation
- Learning-based improvement over time
Intelligent Alert Filtering:
- Contextual notification importance assessment
- User-specific alert customization
- Situation-appropriate communication methods
- Progressive urgency based on event analysis
Expanded Ecosystem Integration
Broader device coordination will enhance effectiveness:
Cross-Platform Security Coordination:
- Unified security state across multiple systems
- Seamless handoff between different protection layers
- Comprehensive logging across diverse devices
- Centralized management of heterogeneous systems
Environmental System Integration:
- HVAC coordination for emergency situations
- Water system management during security events
- Alternative entry methods during emergencies
- Utility control during critical incidents
Community-Level Coordination:
- Optional alert sharing with trusted neighbors
- Neighborhood pattern analysis for broader threats
- Emergency service coordination capabilities
- Community resource activation during widespread events
Enhanced Authentication and Verification
More sophisticated access control will improve security:
Multi-Factor Authentication Expansion:
- Biometric verification integration
- Location-based security level adjustment
- Behavioral authentication patterns
- Continuous verification rather than point-in-time
Contextual Security Adaptation:
- Time-appropriate security level adjustment
- Occupancy-based protection modification
- User-specific security profile application
- Situation-aware authentication requirements
Delegation and Temporary Access Refinement:
- Granular permission control for visitors
- Time-limited access with automatic expiration
- Activity-specific authorization boundaries
- Detailed audit trails for delegated access
Smart Home Security Implementation
Smart switches and plugs form an accessible, affordable foundation for comprehensive home security. By thoughtfully implementing these devices with security as a primary consideration, homeowners can create effective protection systems that deter intruders, provide peace of mind, and enhance overall safety. As the technology continues to evolve, these simple devices will play an increasingly sophisticated role in home security strategies, offering protection that extends far beyond their modest cost and complexity.
